Using Which Social Engineering Principle Might An Attacker Impersonate A Ceo Of A Company?
Phishing attacks are one of the nigh common forms of social engineering attacks. The following epitome shows you an example of a phishing email.
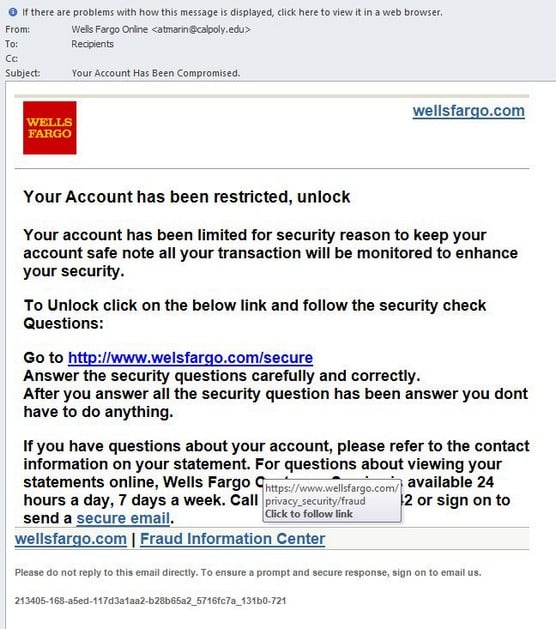 A phishing e-mail.
A phishing e-mail.
Phishing attacks sometimes use a technique chosen pretexting in which the criminal sending the phishing email fabricates a situation that both gains trust from targets besides as underscores the supposed need for the intended victims to act rapidly.
In the phishing email shown, note that the sender, impersonating Wells Fargo bank, included a link to the existent Wells Fargo within the email, just failed to properly disguise the sending address.
Common forms of social engineering attacks include spear phishing emails, smishing, spear smishing, vishing, spear vishing, and CEO fraud.
Phishing
Phishing refers to an endeavour to convince a person to take some action by impersonating a trustworthy party that reasonably may legitimately enquire the user to have such action.For example, a criminal may send an email that appears to have been sent by a major bank and that asks the recipient to click on a link in guild to reset his or her countersign due to a possible data breach. When the user clicks the link, they are directed to a website that appears to belong to the bank, simply is actually a replica run by the criminal.
As such, the criminal uses the fraudulent website to collect usernames and passwords to the banking site.
Spear phishing
Spear phishing refers to phishing attacks that are designed and sent to target a specific person, business, or organisation. If a criminal seeks to obtain credentials into a specific visitor'due south email system, for example, they may send emails crafted specifically for particular targeted individuals within the system.Oftentimes, criminals who spear phish research their targets online and leverage overshared data on social media in social club to craft especially legitimate-sounding emails.
For example, the following type of email is typically a lot more convincing than "Please login to the mail server and reset your countersign.":
"Hello, I am going to exist getting on my flight in x minutes. Can you delight login to the Exchange server and check when my meeting is? For some reason, I cannot go far. You can try to call me by telephone offset for security reasons, but, if yous miss me, only go ahead, cheque the information, and email it to me — as you know that I am getting on a flight that is well-nigh to take off."
CEO fraud
CEO fraud is a social engineering assault that is similar to spear phishing in that it involves a criminal impersonating the CEO or other senior executive of a particular business, but the instructions provided past "the CEO" may be to take an action direct, not to log in to a arrangement, and the goal may not exist to capture usernames and passwords or the similar.The crook, for example, may send an email to the house's CFO instructing them to effect a wire payment to a particular new vendor or to ship all the organizations' W2 forms for the yr to a particular email address belonging to the firm's auditor.
CEO fraud often nets significant returns for criminals and makes employees who fall for the scams appear incompetent. As a upshot, people who fall prey to such scams are often fired from their jobs.
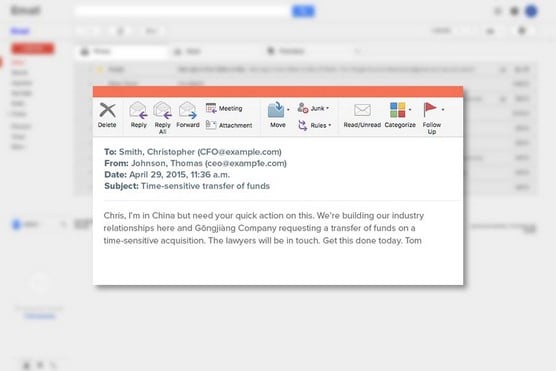 A fraudulent email.
A fraudulent email.
Smishing
Smishing refers to cases of phishing in which the attackers deliver their messages via text messages (SMS) rather than email. The goal may be to capture usernames and passwords or to trick the user into installing malware.Vishing
Vishing, or vox-based phishing, is phishing via POTS — that stands for "plain old telephone service." Aye, criminals utilize old, time-tested methods for scamming people. Today, most such calls are transmitted by voice over IP systems, but, in the end, the scammers are calling people on regular telephones much the same fashion that scammers accept been doing for decades.Whaling
Whaling refers to spear phishing that targets high-contour business executives or government officials.Tampering
Sometimes attackers don't want to disrupt an organization's normal activities, but instead seek to socially engineer past exploiting those activities for fiscal gain. Often, crooks achieve such objectives by manipulating data in transit or as it resides on systems of their targets in a process known as tampering.In a basic case of tampering with data in transit, for example, imagine that a user of online banking has instructed their depository financial institution to wire money to a particular account, only somehow a criminal intercepted the request and changed the relevant routing and account number to their own.
A criminal may also hack into a arrangement and manipulate information for similar purposes. Using the previous case, imagine if a criminal changed the payment address associated with a particular payee so that when the Accounts Payable department makes an online payment. The funds are sent to the incorrect destination (well, at least it is wrong in the eyes of the payer.)
Other social engineering attacks
Additional types of social engineering attacks are popular as well:- Baiting: An attacker sends an email or chat bulletin — or even makes a social media post promises someone a advantage in commutation for taking some action — for example, telling a target that if she completes a survey, they will receive a free particular. Sometimes such promises are real, but, ofttimes they're not and are simply means of incentivizing someone to have a specific action that they would not take otherwise.
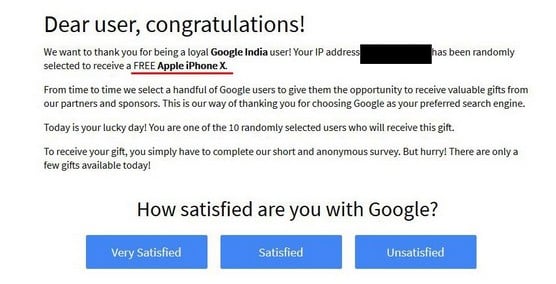 Instance of a baiting message.
Instance of a baiting message.
Sometimes such scammers seek payment of a small shipping fee for the prize, sometimes they distribute malware, and sometimes they collect sensitive information. There is even malware that baits.
Don't confuse baiting with scambaiting. The latter refers to a form of vigilantism in which people pretend to be gullible, would-be victims, and waste scammers' time and resources through repeated interactions, as well every bit (sometimes) collect intelligence about the scammer that tin can be turned over to law enforcement or published on the Cyberspace to warn others of the scammer.
- Quid pro quo: The attacker states that they demand the person to take an activity in guild to render a service for the intended victim. For case, an attacker may pretend to be an It back up manager offering assistance to an employee in installing a new security software update. If the employee cooperates, the criminal walks him through the procedure of installing malware.
- Social media impersonation: Some attackers impersonate people on social media in order to establish social media connections with their victims. The parties being impersonated may be existent people or nonexistent entities. The scammers backside the impersonation beneath and many other such accounts ofttimes contact the people who follow the accounts, pretending to be the author, and request that the followers brand various "investments."
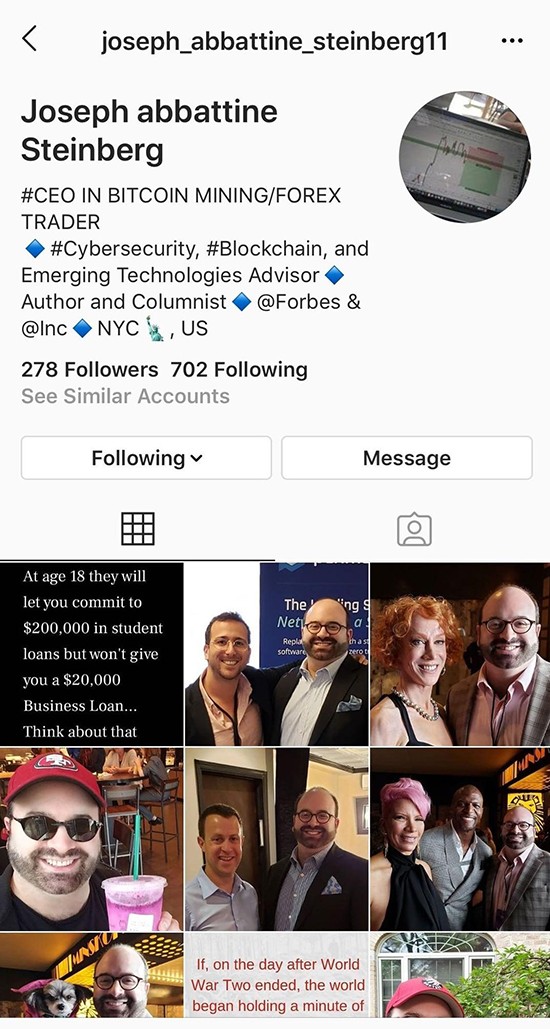 An example of an Instagram account impersonating an author, using his proper name, bio, and primarily photos lifted from his real Instagram business relationship.
An example of an Instagram account impersonating an author, using his proper name, bio, and primarily photos lifted from his real Instagram business relationship. - Tantalizing emails: These emails attempt to fox people into running malware or clicking on poisoned links by exploiting their curiosity, sexual desires, and other characteristics.
- Tailgating: Tailgating is a physical class of social engineering science attack in which the attacker accompanies authorized personnel as they approach a doorway that they, but non the attacker, is authorized to pass and tricks them into letting him laissez passer with the authorized personnel. The attacker may pretend to be searching through a purse for an access card, claim to have forgotten his card, or may simply deed social and follow the authorized party in.
- Imitation alarms: Raising false alarms can too social engineer people into allowing unauthorized people to practise things that they should not be allowed to. Consider the instance in which an assaulter pulls the fire warning inside a building and manages to enter unremarkably secured areas through an emergency door that someone else used to quickly exit due to the so-called emergency.
- Water holing: H2o holing combines hacking and social engineering science by exploiting the fact that people trust sure parties, so, for example, they may click on links when viewing that party's website even if they'd never click on links in an email or text message. Criminals may launch a watering pigsty attack by breaching the relevant site and inserting the poisoned links on it (or even depositing malware directly onto it).
- Virus hoaxes: Criminals exploit the fact that people are concerned virtually cybersecurity, and likely pay undeserved attending to messages that they receive alert most a cyberdanger. Virus hoax emails may contain poisoned links, directly a user to download software, or instruct a user to contact IT support via some e-mail address or spider web page. These attacks come in many flavors — some attacks distribute them as mass emails, while others send them in a highly targeted fashion. Some people consider scareware that scares users into believing that they need to purchase some particular security software to be a class of virus hoax. Others do non considering scareware's "scaring" is done by malware that is already installed, non by a hoax message that pretends that malware is already installed.
- Technical failures: Criminals can easily exploit humans' badgerer with technology problems to undermine various security technologies.
6 principles social engineers exploit
Social psychologist, Robert Beno Cialdini, in his 1984 work published by HarperCollins, Influence: The Psychology of Persuasion, explains six of import, bones concepts that people seeking to influence others oft leverage. Social engineers seeking to play a trick on people often exploit these same 6 principles, so hither's a quick overview of them in the context of data security.The following list helps yous understand and internalize the methods social engineers are probable to use to try to gain your trust:
- Social proof: People tend to do things that they see other people doing.
- Reciprocity: People, in general, oftentimes believe that if someone did something prissy for them, they owe it to that person to practise something overnice dorsum.
- Authority: People tend to obey say-so figures, even when they disagree with the authority figures and fifty-fifty when they think what they're existence asked to exercise is objectionable.
- Likeability: People are, generally speaking, more than easily persuaded by people who they similar than past others.
- Consistency and commitment: If people brand a delivery to reach some goal and internalize that commitment, it becomes role of their self-prototype, and they're likely to attempt.
- Scarcity: If people think that a item resource is deficient, regardless of whether it actually is deficient, they volition desire it, fifty-fifty if they don't need it.
Using Which Social Engineering Principle Might An Attacker Impersonate A Ceo Of A Company?,
Source: https://www.dummies.com/article/technology/cybersecurity/types-of-social-engineering-attacks-266350/
Posted by: robertscoge1939.blogspot.com


0 Response to "Using Which Social Engineering Principle Might An Attacker Impersonate A Ceo Of A Company?"
Post a Comment